This article deals with common credit card skimmers that are installed in thousands of gas pumps as well as other devices that accept credit cards. Skimmers are devices used to steal or copy information from your credit cards. Common criminals tend to utilize simple, inexpensive and easy-to-purchase hardware to steal consumers credit card information, to either use this info personally or sell it to criminal organizations in Russia and other locations.
How They Work:
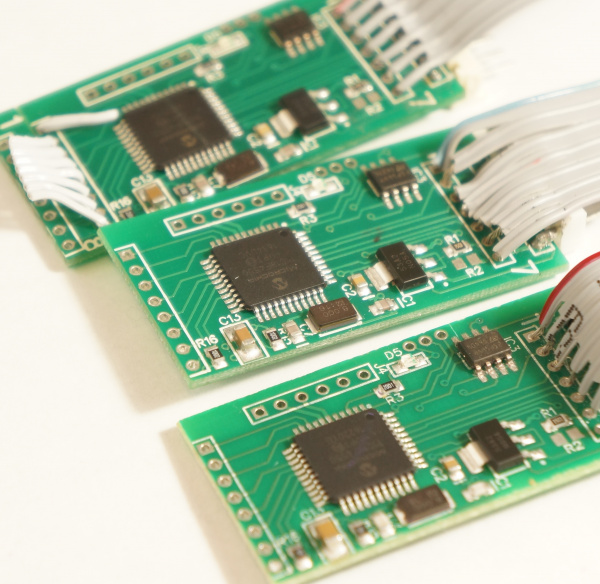
The cheap skimmers found today on the marketplace (China) utilize common Bluetooth technology that can be found on hundreds of legitimate applications, so common today with the surge of IoT (Internet of Things). These skimmer devices can cost as low as $10, including the Bluetooth module that costs $4 or less.
Mostst skimmers main PCB use the popular PIC18F4550 microcontroller to pass-thru data, store data on an EPROM and later extract this data using the Bluetooth module.
The gas pump has a credit card reader that sends serial data, with your credit card information (clear text at 9,600bps), to the pump controller which charges your card. To install the skimmer, the criminals obtain the gas pump key, and in about 30 seconds, can insert the skimmer between the pump’s credit card reader and the pump’s controller. So, when you card is read, the skimmer passes thru the serial data to the pump’s controller, while storing this data in its EPROM. As a consumer, this process is completely transparent to you.
Later, the criminal passes by the pump and without leaving his car, connects to the Bluetooth module, which uploads the collected credit card data to his handheld device.
How to Detect if a Pump has a Skimmer:
If the pump has a Bluetooth skimmer, then it is fairly easy to detect. The Bluetooth module broadcasts as “HC-06” (or “HC-05”, etc.). So, with your smartphone, you can scan and easily detect the Bluetooth broadcast from the skimmer when you are at the pump. You may in fact see several Bluetooth broadcasts from the skimmers installed on the different pumps. These Bluetooth modules come with a default password : 1234, and criminals typically don’t take the time to modify it.
So, if you see these Bluetooth broadcasts at the pump, don’t use the pump. One way to confirm that the Bluetooth broadcast comes from a skimmer is by sending the character “P” to the module with a terminal program. If you receive an “M” in response, then you are certain to have located a skimmer and, if you can, contact the police, as it’s possible that the gas station employees may be in on the scam.
Now you can download an Android app (ATM Skimmer Detector by JDebug) from Google Play to identify the skimmers.
Credit: https://learn.sparkfun.com/tutorials/gas-pump-skimmers